Important note: this post is NOT meant to encourage anyone to carry out a DDoS attack on any website. Rather it is my tongue-in-cheek way of exposing a major flaw in the popular Cloudflare service, in hopes they will take this shit seriously and actually reform their business practices. If you, dear reader, ever DDoS a site for real, I hope you die in a fire.
I use Cloudflare on several sites — for DDoS protection, as a Web Application Firewall, and also for their CDN. I have sites on both free and paid plans with them. Up until now, I thought Cloudflare was a great service — little did I know how easy it is to defeat the entire purpose of using them.
Or to put it another way: Cloudflare is great — until they decide to fuck you over.
Here’s how you defeat Cloudflare:
- Find some images (.jpg, .png) on the target website.
- Create a massive amount of traffic for just those static images, nothing else.
- Cloudflare will incorrectly interpret the traffic as “video streaming”, which apparently violates their ToS.
- Cloudflare will send a ToS violation notice to the site owner.
- About a day later, Cloudflare will start filtering out every image on the site, replacing it with a “this video has been restricted” black and white message, rendering the site ugly as fuck and/or unusable.
- The site owner will argue helplessly with Cloudflare support to no avail — they will have no choice but to disable Cloudflare or find some alternative.
- When they do, catch their real (un-proxied) server IP address soon as Cloudflare is disabled.
- DDoS their server directly at will.
Surely I’m joking, you ask? (No. And don’t call me Shirley…)
I made this discovery entirely by accident. One of my sites allows user generated content, a lot of which is images. Being a strong supporter of free speech, I allow adult content to be uploaded, so yes, a certain percentage of that content is (legal) porn. (That’s not the main purpose of my site, but I don’t censor it.) Keep in mind, we’re talking still images only – no videos are allowed on my site.
Anyway, somebody shared some of that porn to a Chinese porn forum, and man those Chinese people love their porn. That shit went viral like a motherfucker. They hotlinked directly to the images, which were hosted on my server, and soon about a zillion other Chinese forums started copying the same shit.
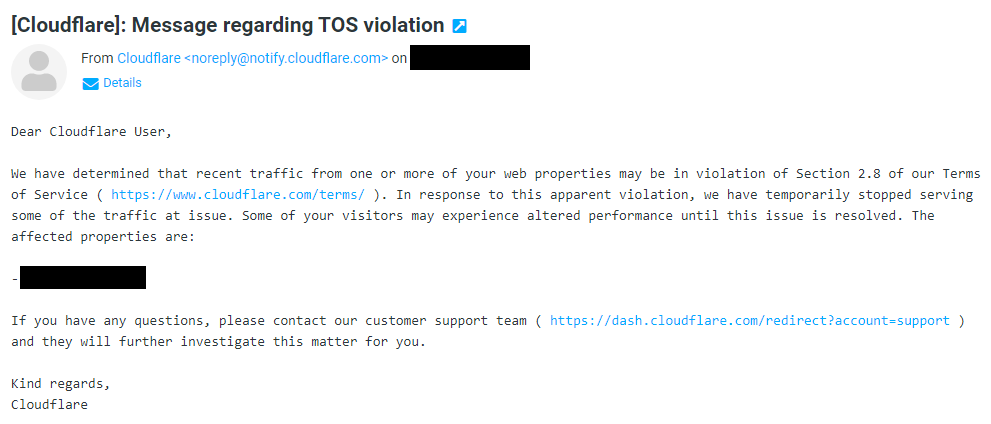
My site normally averages about a 100GB per day in bandwidth through Cloudflare. On the first day of the porn share, that jumped to 400GB, which triggered an automatic nasty email from Cloudflare:
We have determined that recent traffic from one or more of your web properties may be in violation of Section 2.8 of our Terms of Service ( https://www.cloudflare.com/terms/ ). In response to this apparent violation, we have temporarily stopped serving some of the traffic at issue.
I opened a support ticket and discovered that their support is utter shit. I won’t bore you with the details of the whole conversation. Suffice to say, it’s almost impossible to get a straight answer out of them. It took several rounds of messages being exchanged with me having to repeat the same questions over and over — even dumbing them down each time — before I would kinda-sorta get an answer. I wasn’t asking rocket scientist-level stuff here… I just wanted to know 1) what was going on, and 2) how do we fix it.
On day 2, my site’s traffic spiked to an incredible 8TB — in one day! (I told you, those crazy Chinese LOVE their porn, apparently…) At this point, Cloudflare decided to take down EVERY SINGLE IMAGE ON MY SITE. They replaced them all, even silly things like my logo, with a black and white “this video has been restricted” message. Keep in mind, they are doing this to plain, static IMAGE files — not videos!
After 3 or 4 messages they did finally claim the issue was “due to video streaming files”, which is forbidden by their ToS (unless I pay for some separate streaming service of theirs). I explained to them (repeatedly) that there are NO videos anywhere on my site, and I do not stream anything there. Never have. Apparently they were too fucking lazy to just open my site in a browser… if they had they could easily have confirmed this fact.
Well anyway the key here was revealed by them in a later email — if a site gets a big enough traffic spike for “non-HTML” assets, they assume its due to video streaming. They don’t seem to have a way to tell the difference between images and videos!
Meanwhile, I’m getting so many complaints from my users who are now unable to use my site due to Cloudflare’s bullshit. Cloudflare support is becoming a dead end. I tried adding a rule in the Cloudflare settings to completely bypass their cache, but it had no effect. I researched Cloudflare alternatives but couldn’t find anything good without paying hundreds of dollars. So I was left with just one choice — turn off Cloudflare. If I wanted to get my site back online, that was the only option remaining to me. That’s what I did.
Now I knew immediately that this was a big risk — it meant exposing my real server’s IP address to the world, which makes it super easy for anyone to DDoS it if they want to (and on the site in question, somebody already did this to me once before). But again what other choice did I have? Short of spending a shit ton of money for a competing service (not an option) — I was S.O.L.
I was effectively booted off Cloudflare, simply for getting too much traffic.
Being the contrarian thinker that I am, I started thinking about this and realizing… what’s to stop somebody from doing this exact routine — on purpose?
As far as I can tell, nothing. All one has to do is generate enough traffic for image files only — nothing else — and within a day or two the target site will be forced off Cloudflare one way or the other.
One could monitor the target’s DNS records and as soon as you detect the Cloudflare nameservers are gone, you can grab their real server’s IP. At that point you can easily carry out a traditional DDoS attack. That is, assuming you haven’t done enough damage already just targeting their images. Without a CDN, the image traffic alone might be enough to overwhelm their server.
So I ask you — what’s the point of having Cloudflare’s “protection”, when all it takes is a targeted spike in traffic to take you down? That’s like putting bars on all the windows of your house, while leaving the front door unlocked. It makes no sense.
@Cloudflare: please fix your shit. Images != videos. If you want to have bandwidth limits, fine, just fucking say what they are. Don’t trash people’s sites with bogus “this video is restricted” messages when there aren’t any fucking videos. Maybe if people hit a bandwidth limit you should let the request pass through to the origin server, while at least maintaining the firewall and proxy stuff. That way your bandwidth is saved, and the site itself is not trashed with bullshit messages. Am I really asking too much here?

Do you have any experience with vanwa.tech’s “website CDN and DDoS protection”? They apparently have a $5/mo plan, not sure how good it is. They’ve been hosting the most toxic sites like dailystormer.su and 8kun.top for a while now.
As for the Chinese, many sysadmins recommend just blocking all Chinese IP’s (not including HK) because the entire country, including even their government agencies and corporations, uses pirated Windows infected with botnet rootkits. The middle/upperclass of China who can read at least some basic English and have any interest in visiting websites outside the GFW of China already use VPNs. You can easily find regularly-updated country IP lists online for denying in nginx, iptables, apache, etc.
Hadn’t heard of vanwa.tech before, but that looks promising, I may give it a try. Thanks for the tip!
As for China I think I’m beginning to agree with you, blocking the Chinese IPs would avoid a lot of headaches.