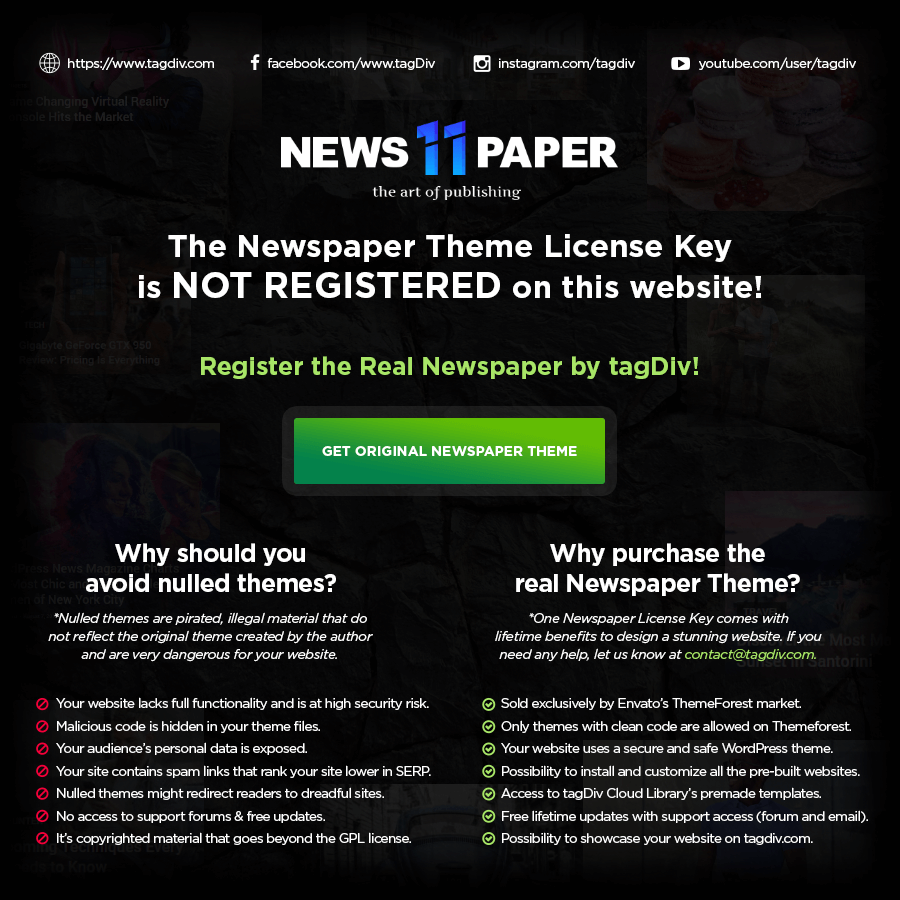
TagDiv, the company which makes the popular WordPress themes Newspaper and Newsmag, embedded malicious code in their products. This code acts as a “kill switch”, allowing them to take down your entire website!
As first reported by Foo Conner at Jekko, this same problem happened to me recently with one of my websites. They took down the entire website — every page — and replaced it with an image like this one:
I was, to put it lightly, livid.
No notice was given. Everything had been working fine for months. Then one day — poof — my website is down. Because I received no notice, it was actually down 3 days before I discovered it! I missed out on untold traffic because of these fuckers.
Let me be clear, TagDiv: it is COMPLETELY, ABSOLUTELY, 100% TOTALLY UNACCEPTABLE TO TAKE DOWN MY WEBSITE WITHOUT PERMISSION, YOU MALICIOUS FUCKING SCAMMERS!!
Ugh.
The really infuriating part is I HAD ALREADY PAID FOR A LICENSE. I bought it on Envato like a good boy. However I do not activate license keys on production websites, because I do not want anything in production ever calling home and updating itself automatically. I have too much PTSD from automated updates taking down sites. That’s why I always test updates first in a controlled staging environment. (Honestly, everyone should.)
So at this point I *could* have entered my license key on my production site, activated it, and moved on, tail between my legs.
But I said NO.
I’m a programmer. I know I just have to find the code doing this to me, and I can fix it myself. There is no way I’m letting these pricks win.
I found the code alright. And it was even scammier looking than I thought. It was stuff right out of the same playbook I’ve seen on hacked websites I’ve been hired to clean up before.
And now, for your benefit, I will tell you how to clean up this malicious code too. That’s assuming switching to some other theme from an actual reputable company is not an option, and you must continue using TagDiv’s shit.
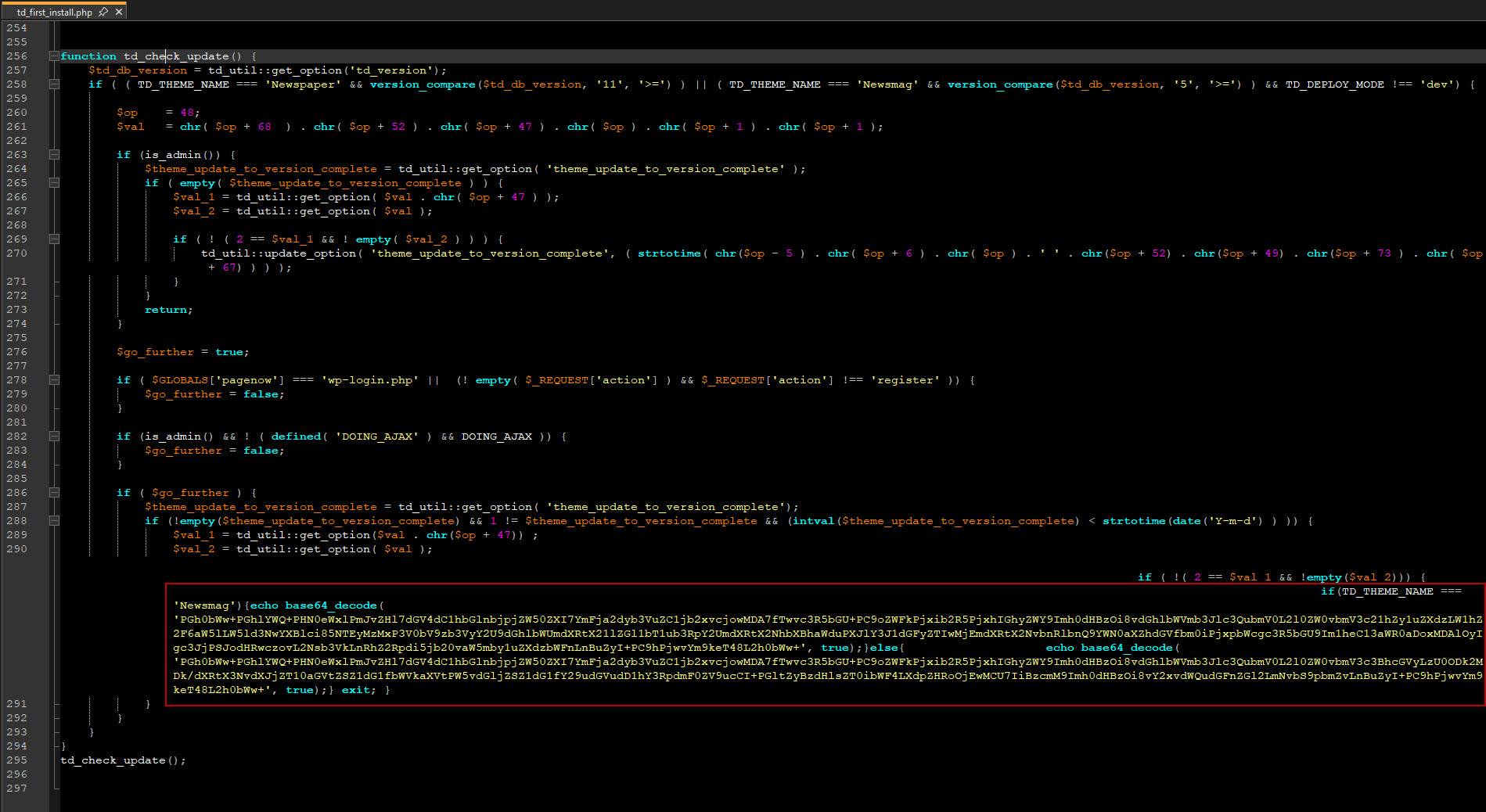
TagDiv’s themes come with a mandatory plugin called “tagDiv Composer”. The malicious code is here, in the file /wp-content/plugins/td-composer/legacy/common/wp_booster/td_first_install.php. Look for the function td_check_update. Remove the entire function, and the call to it. In this screenshot, that would be everything from line 256 to the end for the file:
They’ve obfuscated the malicious code (as bad actors always do) in base64 strings. They’ve used chr() codes in a lot of places, rather than plain text, to further make it harder to see what’s really going on. Importantly — make sure you have Word Wrap enabled. They hiked the malicious payload way off to the right of a zillion spaces, hoping it would be off the edge of the screen where you wouldn’t see it. (I confess this trick worked on me during my first pass searching through the files… gg TagDiv, you wasted another 5 minutes of my life.)
There are other places in the code where they can call home for various purposes… you can easily search for references to tagdiv.com, themesafe.com, and themeforest.net and handle these as you wish. I did so myself in the spirit of being thorough, but I don’t think it was necessary. The td_check_update function was the only spot where the really malicious code is.
So, again, if you’re forced to continue using Newspaper or Newsmag theme for any reason, at least do this to remove the kill switch from your site.
If anyone has a recommendation for a better theme alternative please let me know in the comments!
And, finally, FUCK YOU TAGDIV.
P.S. There is an unrelated major vulnerability in the TagDiv Composer plugin which led to many, many websites getting hacked. Please make sure you’re not using an affected version, or else patch it. (This is just more proof TagDiv are shitty, incompetent developers.)